Intro
Discover the 5 ways the Air Force conducts cyber warfare operations, including network exploitation, cyber espionage, and digital combat. Learn how the Air Force protects national security through cyber defense and offense, using advanced technologies and tactics to stay ahead of cyber threats and adversaries in the digital battlefield.
The increasing importance of cybersecurity in today's digital age has led to the development of advanced cyber warfare strategies by various military organizations, including the Air Force. Cyber warfare operations are designed to disrupt, disable, or destroy an adversary's ability to use their computer systems and networks. The Air Force conducts cyber warfare operations to support national security objectives, protect its own networks and systems, and enhance its military capabilities.

The Air Force has developed a comprehensive approach to conducting cyber warfare operations, which includes the following five ways:
1. Network Exploitation
Network exploitation involves the use of various techniques to gain unauthorized access to an adversary's computer networks and systems. The Air Force uses advanced tools and techniques to identify vulnerabilities in an adversary's networks and exploit them to gain access to sensitive information. Once inside the network, the Air Force can gather intelligence, disrupt operations, or destroy critical infrastructure.
Techniques Used in Network Exploitation
- Phishing: a technique used to trick users into revealing sensitive information such as passwords or financial information.
- Malware: software designed to harm or exploit a computer system.
- Social engineering: a technique used to manipulate individuals into revealing sensitive information.

2. Network Attack
Network attack involves the use of various techniques to disrupt or destroy an adversary's computer networks and systems. The Air Force uses advanced tools and techniques to launch network attacks, which can include denial-of-service (DoS) attacks, distributed denial-of-service (DDoS) attacks, and malware attacks.
Techniques Used in Network Attack
- Denial-of-service (DoS) attack: a type of attack that floods a network with traffic in an attempt to overwhelm it and make it unavailable to users.
- Distributed denial-of-service (DDoS) attack: a type of attack that uses multiple systems to flood a network with traffic.
- Malware attack: a type of attack that uses software designed to harm or exploit a computer system.

3. Network Defense
Network defense involves the use of various techniques to protect an Air Force network from cyber threats. The Air Force uses advanced tools and techniques to detect, prevent, and respond to cyber threats. This includes the use of firewalls, intrusion detection systems, and encryption.
Techniques Used in Network Defense
- Firewalls: network security systems that monitor and control incoming and outgoing network traffic.
- Intrusion detection systems: systems that detect and alert on potential security threats.
- Encryption: the process of converting plaintext into unreadable ciphertext to protect data.
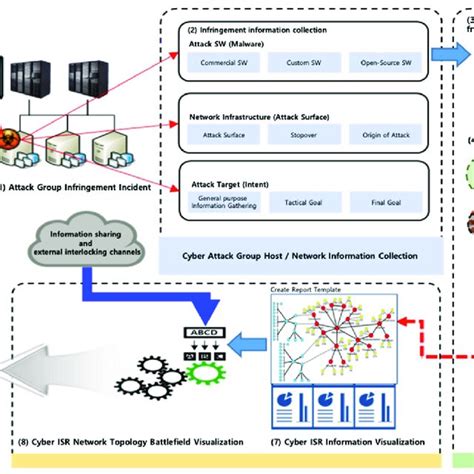
4. Cyber Intelligence, Surveillance, and Reconnaissance (ISR)
Cyber ISR involves the use of various techniques to gather information about an adversary's computer networks and systems. The Air Force uses advanced tools and techniques to gather information about an adversary's networks, including their strengths, weaknesses, and vulnerabilities.
Techniques Used in Cyber ISR
- Network mapping: the process of creating a diagram of an adversary's network to identify potential vulnerabilities.
- Vulnerability scanning: the process of identifying potential vulnerabilities in an adversary's network.
- Social engineering: a technique used to manipulate individuals into revealing sensitive information.
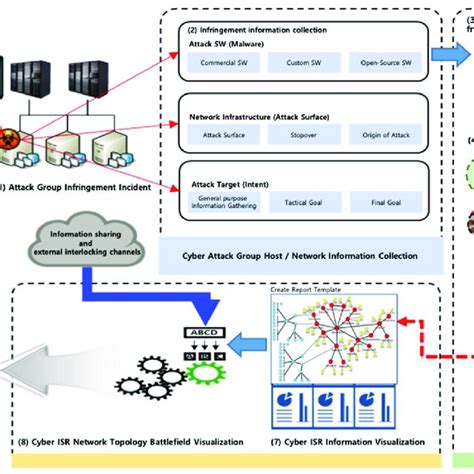
5. Cyber Training and Exercises
Cyber training and exercises involve the use of various techniques to train and exercise Air Force personnel in cyber warfare operations. The Air Force uses advanced tools and techniques to simulate cyber threats and test the readiness of its personnel.
Techniques Used in Cyber Training and Exercises
- Simulated cyber attacks: simulated attacks used to test the readiness of Air Force personnel.
- Cyber exercises: exercises used to train and test Air Force personnel in cyber warfare operations.
- Cyber competitions: competitions used to test the skills of Air Force personnel in cyber warfare operations.

In conclusion, the Air Force conducts cyber warfare operations to support national security objectives, protect its own networks and systems, and enhance its military capabilities. The five ways the Air Force conducts cyber warfare operations are network exploitation, network attack, network defense, cyber ISR, and cyber training and exercises. Each of these areas requires advanced tools and techniques, as well as highly trained personnel.
We encourage you to share your thoughts on the importance of cyber warfare operations in the comments section below. How do you think the Air Force should prioritize its cyber warfare operations? What do you think are the most significant challenges facing the Air Force in the cyber domain?
Cyber Warfare Operations Image Gallery








What is cyber warfare?
+Cyber warfare is the use of technology to disrupt, disable, or destroy an adversary's ability to use their computer systems and networks.
What are the five ways the Air Force conducts cyber warfare operations?
+The five ways the Air Force conducts cyber warfare operations are network exploitation, network attack, network defense, cyber ISR, and cyber training and exercises.
What is network exploitation?
+Network exploitation involves the use of various techniques to gain unauthorized access to an adversary's computer networks and systems.
What is cyber ISR?
+Cyber ISR involves the use of various techniques to gather information about an adversary's computer networks and systems.
Why is cyber training and exercises important?
+Cyber training and exercises are important to train and test Air Force personnel in cyber warfare operations, and to ensure they are ready to respond to cyber threats.
