Intro
Unlock the world of cyber security specialties and discover the diverse career paths within this in-demand field. From threat intelligence to incident response, penetration testing to security architecture, explore the various roles and required skills to stay ahead of cyber threats and protect sensitive information.
In today's digital age, cyber security has become a vital aspect of protecting individuals, businesses, and governments from the ever-growing threat of cyber-attacks. As the demand for skilled cyber security professionals continues to rise, various specialties have emerged within the field. In this article, we will delve into the different cyber security specialties, their roles, and the skills required to succeed in each area.
What is Cyber Security?
Cyber security refers to the practice of protecting digital information, networks, and systems from unauthorized access, use, disclosure, disruption, modification, or destruction. This includes protecting against malware, viruses, phishing attacks, denial-of-service (DoS) attacks, and other types of cyber threats.
Cyber Security Specialties
Cyber security is a broad field that encompasses various specialties, each requiring unique skills and expertise. Here are some of the most in-demand cyber security specialties:
1. Network Security
Network security involves protecting computer networks from cyber threats. Network security specialists design and implement secure network architectures, configure firewalls and intrusion detection systems, and monitor network traffic for signs of unauthorized access.

2. Cloud Security
Cloud security involves protecting cloud-based infrastructure, applications, and data from cyber threats. Cloud security specialists ensure the secure deployment of cloud-based systems, configure cloud security controls, and monitor cloud-based infrastructure for signs of unauthorized access.

3. Cyber Intelligence
Cyber intelligence involves gathering and analyzing information about cyber threats to predict and prevent future attacks. Cyber intelligence specialists collect and analyze threat data, identify patterns and trends, and provide recommendations for improving cyber security defenses.

4. Incident Response
Incident response involves responding to and managing cyber security incidents, such as data breaches or ransomware attacks. Incident response specialists develop incident response plans, coordinate incident response efforts, and provide training and awareness programs to prevent future incidents.

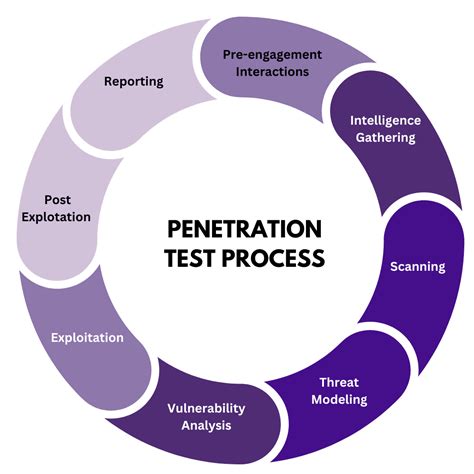
5. Penetration Testing
Penetration testing involves simulating cyber-attacks on computer systems, networks, or applications to test their defenses. Penetration testers use various techniques to bypass security controls and identify vulnerabilities, providing recommendations for improving cyber security defenses.

6. Security Consulting
Security consulting involves providing expert advice and guidance on cyber security matters to organizations. Security consultants assess an organization's cyber security posture, identify vulnerabilities, and provide recommendations for improving cyber security defenses.

7. Digital Forensics
Digital forensics involves collecting, analyzing, and preserving digital evidence to investigate cyber crimes. Digital forensics specialists use various tools and techniques to analyze digital evidence, identify the source of a cyber-attack, and provide expert testimony in court.

8. Cyber Security Management
Cyber security management involves overseeing and coordinating an organization's cyber security efforts. Cyber security managers develop cyber security policies, procedures, and standards, and ensure compliance with regulatory requirements.

9. Artificial Intelligence and Machine Learning Security
Artificial intelligence and machine learning security involves protecting AI and ML systems from cyber threats. AI and ML security specialists design and implement secure AI and ML architectures, configure AI and ML security controls, and monitor AI and ML systems for signs of unauthorized access.

10. Internet of Things (IoT) Security
IoT security involves protecting IoT devices and systems from cyber threats. IoT security specialists design and implement secure IoT architectures, configure IoT security controls, and monitor IoT systems for signs of unauthorized access.

Conclusion
Cyber security is a diverse and rapidly evolving field, with various specialties requiring unique skills and expertise. As the demand for skilled cyber security professionals continues to rise, it's essential to understand the different cyber security specialties and the skills required to succeed in each area. Whether you're interested in network security, cloud security, or AI and ML security, there's a cyber security specialty that's right for you.
Gallery of Cyber Security Specialties
Cyber Security Specialties Image Gallery









FAQs
What is cyber security?
+Cyber security is the practice of protecting digital information, networks, and systems from unauthorized access, use, disclosure, disruption, modification, or destruction.
What are the different cyber security specialties?
+There are several cyber security specialties, including network security, cloud security, cyber intelligence, incident response, penetration testing, security consulting, digital forensics, cyber security management, AI and ML security, and IoT security.
What skills are required to succeed in cyber security?
+Cyber security professionals require a range of skills, including technical skills, analytical skills, problem-solving skills, and communication skills.
I hope this article has provided you with a comprehensive understanding of the different cyber security specialties and the skills required to succeed in each area. Remember to stay up-to-date with the latest developments in cyber security and to continually develop your skills to stay ahead in this rapidly evolving field.
