Intro
Discover 5 ways to remove delegate access, revoking shared permissions and regaining control over your accounts, calendars, and emails with ease, using simple steps and best practices for access management and security.
Removing delegate access is a crucial step in maintaining the security and integrity of your digital accounts and systems. Delegate access allows others to manage or access your accounts on your behalf, which can be convenient but also poses risks if not properly managed. Whether you're looking to remove delegate access from your email, calendar, or other shared resources, it's essential to understand the steps involved and the importance of regularly reviewing who has access to your digital assets.
The ability to delegate access is a feature in many digital systems, including email services like Gmail, Outlook, and iCloud, as well as calendar and file-sharing platforms. This feature enables you to grant others the ability to read, send, and manage emails or events on your behalf. However, there are scenarios where you might need to revoke these permissions, such as when an employee leaves a company, a personal assistant is no longer needed, or if you suspect unauthorized access.
Understanding the reasons behind removing delegate access is as important as knowing how to do it. Security is a primary concern, as unauthorized access can lead to data breaches, identity theft, and other malicious activities. Moreover, in professional settings, removing delegate access is part of the offboarding process for employees who are leaving the company, ensuring that company data and systems are protected.
Before diving into the steps to remove delegate access, it's crucial to note that the process can vary significantly depending on the platform or service you're using. Most services provide straightforward instructions within their settings or help sections. However, the general principles of identifying the delegate access feature, selecting the account or permission you wish to revoke, and confirming the removal are consistent across most platforms.
Understanding Delegate Access

Delegate access is a powerful tool that allows for the efficient management of digital assets. It's commonly used in both personal and professional contexts to streamline tasks and improve collaboration. However, with great power comes great responsibility, and it's essential to monitor and control who has access to your accounts.
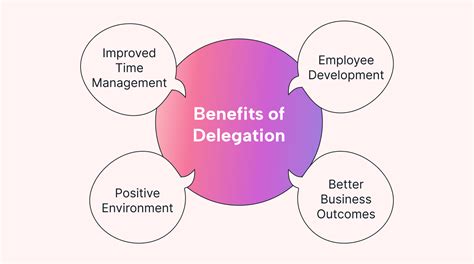
Benefits of Delegate Access
The benefits of delegate access include enhanced productivity, as tasks can be delegated to others, allowing for more efficient time management. It also facilitates collaboration, especially in work environments, by enabling teams to work together seamlessly on projects and share information.Risks Associated with Delegate Access
Despite its benefits, delegate access also comes with risks. The primary concern is security, as granting access to your accounts can make them vulnerable to unauthorized use or data breaches. Additionally, there's the risk of misuse, where the delegated individual might use the access for purposes not intended by the account owner.Steps to Remove Delegate Access
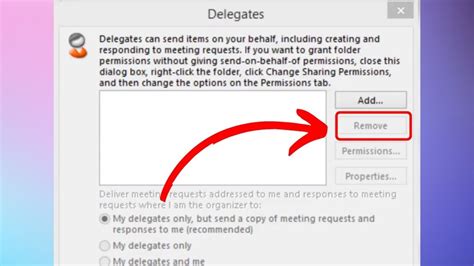
Removing delegate access involves several steps that are generally applicable across different platforms. Here’s a step-by-step guide:
-
Access Your Account Settings: The first step is to log into your account and navigate to the settings section. This is usually found in a dropdown menu under your profile picture or name.
-
Find the Delegate Access Section: Once in the settings, look for a section related to account access, permissions, or delegates. The exact wording can vary, but it should be related to managing who has access to your account.
-
Select the Delegate: Identify the individual or account from which you wish to remove delegate access. This might involve checking boxes next to their names or selecting their profiles from a list.
-
Remove Access: After selecting the delegate, you should see an option to remove or revoke their access. This might be a button, a link, or a toggle switch, depending on the platform's interface.
-
Confirm Removal: Finally, confirm that you want to remove the delegate access. This step is crucial as it ensures that the action is intentional and helps prevent accidental removals.
Platform-Specific Instructions
While the general steps are similar, the specifics can vary significantly between platforms. For instance, removing delegate access in Gmail involves going to the "Settings" > "Accounts and Import" > "Grant access to your account," and then selecting "Delete" next to the account you wish to remove. In Outlook, you would go to "File" > "Account Settings" > "Delegate Access," and then remove the delegate.Best Practices for Managing Delegate Access
Managing delegate access effectively is key to maintaining the security and integrity of your digital assets. Here are some best practices:
- Regularly Review Access: Periodically review who has access to your accounts to ensure that permissions are up to date and appropriate.
- Use Least Privilege Principle: Only grant the level of access necessary for the task at hand. This minimizes the risk of data breaches or misuse.
- Monitor Account Activity: Keep an eye on your account activity to quickly identify and address any suspicious behavior.
- Implement Two-Factor Authentication: Adding an extra layer of security can help protect your accounts even if delegate access is compromised.
Common Mistakes to Avoid
When managing delegate access, there are several common mistakes to avoid. These include granting access to too many people, not regularly reviewing permissions, and not using secure methods to share access. By being mindful of these potential pitfalls, you can better protect your digital assets.Conclusion and Final Thoughts

In conclusion, removing delegate access is an important aspect of digital security and asset management. By understanding the benefits and risks associated with delegate access and following the steps to remove it when necessary, individuals can better protect their digital presence. Remember, managing delegate access is an ongoing process that requires regular attention to ensure that your accounts and data remain secure.
Future of Delegate Access Management
As technology evolves, the way we manage delegate access will likely become more sophisticated. With advancements in AI and security technologies, we can expect more streamlined and secure methods of granting and revoking access. However, the fundamental principles of carefully managing who has access to your digital assets will remain crucial.Delegate Access Management Image Gallery




What is delegate access and why is it used?
+Delegate access is a feature that allows others to manage or access your digital accounts on your behalf. It's commonly used for convenience and to facilitate collaboration in personal and professional settings.
How do I remove delegate access from my email account?
+The process varies by email service provider, but generally involves going to your account settings, finding the section on delegate access or account permissions, selecting the account you wish to remove, and confirming the removal.
What are the risks associated with delegate access?
+The primary risks include security breaches, data misuse, and unauthorized access to your accounts. It's essential to manage delegate access carefully and regularly review permissions.
If you have found this information on removing delegate access helpful, we invite you to share your thoughts or questions in the comments below. Your feedback is invaluable in helping us provide the most relevant and useful content. Additionally, if you know someone who might benefit from understanding how to manage delegate access, please consider sharing this article with them. By spreading awareness about digital security and best practices for managing access, we can all contribute to a safer online community.
