Intro
Master the Grayzone: Discover the 5 Essential Tools of the Trade to stay ahead in the world of covert operations, special forces, and asymmetric warfare. Learn about the critical gear and tactics used by professionals in the gray area between military and civilian life, including surveillance, infiltration, and escape tools.
In the ever-evolving world of cybersecurity, threat actors have become increasingly sophisticated in their tactics, techniques, and procedures (TTPs). One of the most notorious threat actor groups is the GRU's (Russian military intelligence) 85th Special Services Center, also known as "Fancy Bear" or "APT28." They are known for their high-profile attacks, including the infamous Democratic National Committee (DNC) hack in 2016. Grayzone, a well-known cybersecurity firm, has been at the forefront of tracking and analyzing the activities of Fancy Bear and other threat actors. In this article, we will delve into five essential Grayzone tools of the trade that have been identified as being used by Fancy Bear.
Understanding the Grayzone Context
Before diving into the tools, it's essential to understand the context in which Grayzone operates. Grayzone is a cybersecurity firm that specializes in tracking and analyzing threat actors, particularly those with nation-state backing. They provide critical insights and threat intelligence to help organizations defend against sophisticated cyber attacks. Fancy Bear, being one of the most notorious threat actors, has been a primary focus of Grayzone's research.
Tool 1: Mshta.exe
What is Mshta.exe?
Mshta.exe is a legitimate Windows utility that is used to execute Microsoft HTML Applications (HTAs). However, Fancy Bear has been known to use Mshta.exe as a tool for executing malicious code.

How is Mshta.exe used by Fancy Bear?
Fancy Bear uses Mshta.exe to execute malicious code, often in the form of an HTA file. This allows them to bypass traditional security measures and execute code on the targeted system.
Tool 2: PowerShell
What is PowerShell?
PowerShell is a powerful task automation and configuration management framework from Microsoft. It's widely used by system administrators for legitimate purposes.
How is PowerShell used by Fancy Bear?
Fancy Bear uses PowerShell to execute malicious code, often in the form of a script. This allows them to interact with the targeted system and perform various malicious activities, such as data exfiltration or lateral movement.
Tool 3: RemCom
What is RemCom?
RemCom is a remote access tool (RAT) that allows Fancy Bear to remotely access and control targeted systems.
How is RemCom used by Fancy Bear?
Fancy Bear uses RemCom to remotely access and control targeted systems, allowing them to perform various malicious activities, such as data exfiltration or installing additional malware.
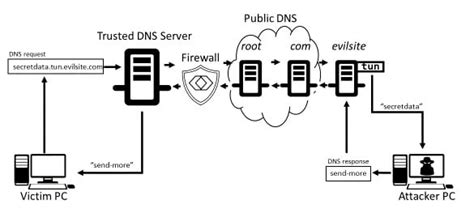
Tool 4: Fancy Bear's Custom DNS Tunnel
What is Fancy Bear's Custom DNS Tunnel?
Fancy Bear's custom DNS tunnel is a tool used to exfiltrate data from targeted systems.
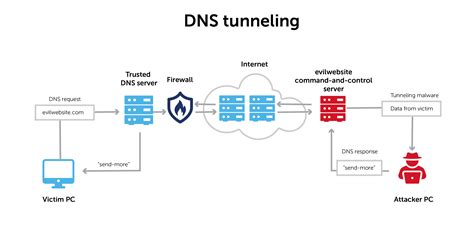
How is Fancy Bear's Custom DNS Tunnel used?
Fancy Bear uses their custom DNS tunnel to exfiltrate data from targeted systems, often in a way that is difficult to detect.
Tool 5: X-Agent
What is X-Agent?
X-Agent is a malware toolkit used by Fancy Bear to infect targeted systems.

How is X-Agent used by Fancy Bear?
Fancy Bear uses X-Agent to infect targeted systems, often through phishing campaigns or exploiting vulnerabilities.
Gallery of Fancy Bear's Tools
Fancy Bear's Tools Image Gallery





FAQs
What is Grayzone?
+Grayzone is a cybersecurity firm that specializes in tracking and analyzing threat actors, particularly those with nation-state backing.
What is Fancy Bear?
+Fancy Bear is a notorious threat actor group, also known as "APT28," that is believed to be sponsored by the Russian government.
What is Mshta.exe?
+Mshta.exe is a legitimate Windows utility that is used to execute Microsoft HTML Applications (HTAs).
We hope this article has provided valuable insights into the five essential Grayzone tools of the trade used by Fancy Bear. By understanding these tools and their tactics, organizations can better defend themselves against sophisticated cyber attacks. Stay vigilant and stay informed!
