Intro
Enhance military cyber security with cutting-edge defense strategies, protecting sensitive information from sophisticated threats. Discover how advanced threat intelligence, AI-powered detection, and proactive incident response can bolster national security, prevent data breaches, and safeguard critical infrastructure against cyber attacks and malicious actors.
In today's digital age, military organizations face an unprecedented array of cyber threats. As the world becomes increasingly interconnected, the risk of cyber attacks on military networks, systems, and personnel grows exponentially. It is imperative for military organizations to prioritize cyber security and develop advanced defense strategies to protect their sensitive information and critical infrastructure.
The importance of military cyber security cannot be overstated. Cyber attacks can have devastating consequences, including the theft of sensitive information, disruption of critical operations, and even physical harm to personnel and equipment. Moreover, the nature of cyber warfare is constantly evolving, with new threats and vulnerabilities emerging daily. To stay ahead of these threats, military organizations must adopt a proactive and adaptive approach to cyber security.

Understanding the Threat Landscape
To develop effective defense strategies, military organizations must first understand the threat landscape. This includes identifying the types of threats they face, such as malware, phishing, and denial-of-service (DoS) attacks. It also involves understanding the motivations and tactics of potential adversaries, including nation-state actors, terrorist organizations, and rogue individuals.
One of the most significant threats to military cyber security is the insider threat. This refers to the risk of authorized personnel intentionally or unintentionally compromising sensitive information or systems. To mitigate this risk, military organizations must implement robust access controls, monitoring, and incident response protocols.
Types of Cyber Threats
- Malware: Malicious software designed to damage or disrupt computer systems.
- Phishing: Social engineering attacks designed to trick users into divulging sensitive information.
- Denial-of-Service (DoS) attacks: Overwhelming a system with traffic in order to make it unavailable.
- Insider threats: Authorized personnel intentionally or unintentionally compromising sensitive information or systems.
Advanced Defense Strategies
To combat the evolving threat landscape, military organizations must adopt advanced defense strategies. These include:
Artificial Intelligence (AI) and Machine Learning (ML)
AI and ML can be used to detect and respond to cyber threats in real-time. These technologies can analyze vast amounts of data to identify patterns and anomalies, enabling swift and effective incident response.
Cloud Security
As military organizations increasingly rely on cloud-based services, cloud security is becoming a critical concern. This includes implementing robust access controls, encrypting sensitive data, and monitoring cloud-based systems for suspicious activity.
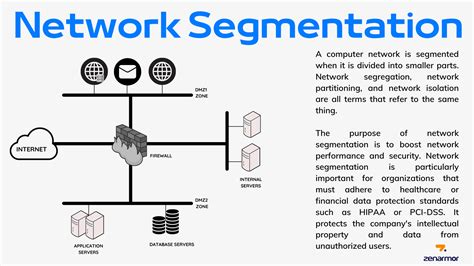
Network Segmentation
Network segmentation involves dividing a network into smaller, isolated segments. This can help prevent lateral movement in the event of a breach, reducing the attack surface and minimizing the risk of sensitive information being compromised.
Incident Response
Effective incident response is critical to minimizing the impact of a cyber attack. This includes having a well-trained incident response team, developing a comprehensive incident response plan, and conducting regular exercises and training.
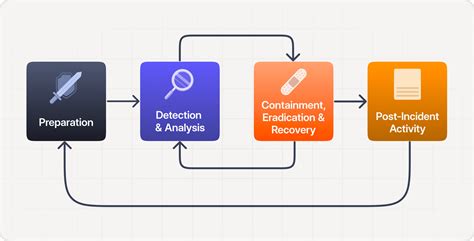
Cyber Security Awareness and Training
Cyber security awareness and training are essential to preventing cyber attacks. Military personnel must be educated on the risks and consequences of cyber threats, as well as the best practices for protecting sensitive information and systems.
Cyber Security Awareness
- Educating personnel on the risks and consequences of cyber threats.
- Raising awareness of potential threats and vulnerabilities.
- Promoting a culture of cyber security within the organization.
Cyber Security Training
- Providing training on cyber security best practices and protocols.
- Conducting regular exercises and training to ensure personnel are prepared to respond to cyber threats.
- Offering specialized training for incident response teams and other critical personnel.
Collaboration and Information Sharing
Collaboration and information sharing are critical to effective cyber security. Military organizations must work together to share threat intelligence, best practices, and lessons learned.
Information Sharing
- Sharing threat intelligence and incident response information.
- Collaborating on cyber security research and development.
- Participating in joint cyber security exercises and training.
International Cooperation
- Collaborating with international partners to share cyber security best practices and threat intelligence.
- Participating in international cyber security forums and working groups.
- Developing international standards and protocols for cyber security.

Gallery of Military Cyber Security
Military Cyber Security Image Gallery






What is the most significant threat to military cyber security?
+The most significant threat to military cyber security is the insider threat, which refers to the risk of authorized personnel intentionally or unintentionally compromising sensitive information or systems.
What is the role of artificial intelligence in military cyber security?
+Artificial intelligence can be used to detect and respond to cyber threats in real-time, analyzing vast amounts of data to identify patterns and anomalies.
Why is international cooperation important for military cyber security?
+International cooperation is essential for sharing threat intelligence, best practices, and lessons learned, as well as developing international standards and protocols for cyber security.
We hope this article has provided valuable insights into the importance of military cyber security and the advanced defense strategies required to protect sensitive information and critical infrastructure. By prioritizing cyber security and adopting a proactive and adaptive approach, military organizations can stay ahead of the evolving threat landscape and ensure the security and integrity of their systems and personnel.
