Intro
Discover how cyber IT specialists safeguard your sensitive information with 7 expert strategies. Learn about threat detection, encryption methods, and network security measures to prevent cyber attacks, data breaches, and ransomware. Ensure your digital assets are protected with these proactive cybersecurity techniques and stay ahead of potential threats.
Understanding the Importance of Cyber IT Specialists in Protecting Your Data

In today's digital age, protecting sensitive data has become a top priority for individuals and organizations alike. With the increasing threat of cyber-attacks, data breaches, and identity theft, it's more important than ever to have a robust cybersecurity system in place. This is where Cyber IT specialists come in – highly trained professionals who specialize in protecting your data from potential threats. In this article, we'll explore the seven ways Cyber IT specialists protect your data and why they're essential in today's digital landscape.
1. Implementing Firewalls and Intrusion Detection Systems
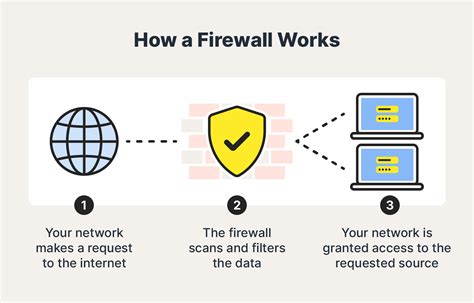
One of the primary ways Cyber IT specialists protect your data is by implementing firewalls and intrusion detection systems. These systems act as a barrier between your network and the internet, blocking unauthorized access and detecting potential threats. Firewalls can be configured to allow or block specific types of traffic, ensuring that only authorized users can access your network.
How Firewalls Work
Firewalls work by examining incoming and outgoing network traffic and blocking any traffic that doesn't meet predetermined security criteria. This includes blocking traffic from unknown sources, blocking traffic that's not encrypted, and blocking traffic that's attempting to access sensitive areas of the network.
2. Conducting Regular Security Audits

Cyber IT specialists conduct regular security audits to identify potential vulnerabilities in your network. These audits involve scanning your network for weaknesses, identifying areas that need improvement, and implementing measures to strengthen your security posture.
What to Expect from a Security Audit
A security audit typically involves the following steps:
- Identifying potential vulnerabilities in your network
- Assessing the severity of these vulnerabilities
- Prioritizing remediation efforts based on risk
- Implementing measures to strengthen your security posture
3. Implementing Encryption Protocols
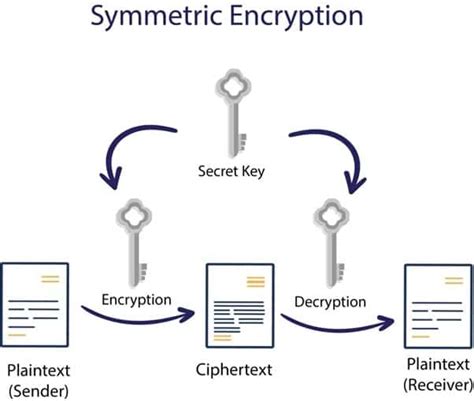
Encryption protocols are an essential part of protecting your data. Cyber IT specialists implement encryption protocols to ensure that data is protected both in transit and at rest. This includes encrypting data stored on servers, laptops, and mobile devices, as well as encrypting data transmitted over the internet.
Types of Encryption Protocols
There are several types of encryption protocols, including:
- Symmetric encryption (AES, DES)
- Asymmetric encryption (RSA, elliptic curve cryptography)
- Hash functions (SHA-256, MD5)
4. Developing Incident Response Plans

Cyber IT specialists develop incident response plans to ensure that your organization is prepared in the event of a security breach. These plans outline the steps to take in the event of a breach, including containment, eradication, recovery, and post-incident activities.
Key Components of an Incident Response Plan
An incident response plan should include the following components:
- Incident classification and initial response
- Containment and eradication procedures
- Recovery procedures
- Post-incident activities (e.g., lessons learned, documentation)
5. Implementing Multi-Factor Authentication
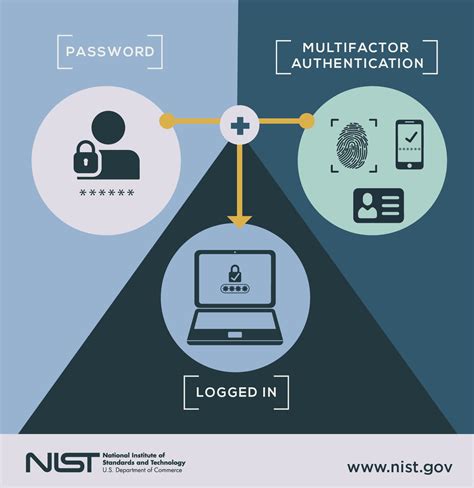
Multi-factor authentication is an essential security measure that Cyber IT specialists implement to protect your data. This involves requiring users to provide multiple forms of verification before accessing your network or sensitive data.
Types of Multi-Factor Authentication
There are several types of multi-factor authentication, including:
- Something you know (password, PIN)
- Something you have (smart card, token)
- Something you are (biometric authentication)
6. Providing Employee Training and Awareness

Cyber IT specialists recognize that employees are often the weakest link in the security chain. To address this, they provide regular training and awareness programs to educate employees on security best practices, phishing attacks, and other potential threats.
Key Components of Employee Training and Awareness
Employee training and awareness programs should include the following components:
- Security best practices (password management, safe browsing)
- Phishing attack recognition and response
- Incident reporting procedures
7. Staying Up-to-Date with Emerging Threats

Cyber IT specialists stay up-to-date with emerging threats by attending conferences, participating in online forums, and following security news and blogs. This ensures that they're aware of the latest threats and can implement measures to protect your data.
Staying Ahead of Emerging Threats
Staying ahead of emerging threats requires:
- Continuous monitoring of security news and blogs
- Participation in online forums and discussions
- Attendance at security conferences and workshops
Cyber IT Specialists Image Gallery










What is the role of a Cyber IT specialist?
+Cyber IT specialists play a crucial role in protecting your data from potential threats. They implement firewalls and intrusion detection systems, conduct regular security audits, and develop incident response plans, among other things.
How do Cyber IT specialists stay up-to-date with emerging threats?
+Cyber IT specialists stay up-to-date with emerging threats by attending conferences, participating in online forums, and following security news and blogs.
What is the importance of multi-factor authentication?
+Multi-factor authentication is an essential security measure that requires users to provide multiple forms of verification before accessing your network or sensitive data.
In conclusion, Cyber IT specialists play a vital role in protecting your data from potential threats. By implementing firewalls and intrusion detection systems, conducting regular security audits, developing incident response plans, and staying up-to-date with emerging threats, they ensure that your data is safe and secure. If you're concerned about the security of your data, consider hiring a Cyber IT specialist to protect your digital assets.
What are your thoughts on the importance of Cyber IT specialists in protecting your data? Share your comments and questions below!
