Intro
Uncover the hidden meaning behind numbers in military code. Learn how to decode military secrets and understand the significance of numerical codes in military communication. From tactical operations to encrypted messages, discover the role of numbers in military strategy and gain insight into the world of military cryptography and coding systems.
Numbers have been an integral part of military operations for centuries. From ancient times to the present day, numbers have played a crucial role in encoding and decoding sensitive information. Military code, also known as cryptography, relies heavily on numbers to conceal messages and ensure secure communication.

Understanding numbers in military code is a complex task that requires knowledge of various techniques and methods. From substitution ciphers to transposition ciphers, numbers are used to scramble and unscramble messages. In this article, we will delve into the world of military code and explore the significance of numbers in this secretive realm.
History of Military Code
The use of codes and ciphers in military communication dates back to ancient civilizations. The earliest recorded use of cryptography was by the Egyptians around 1900 BCE. The Egyptians used a simple substitution cipher, replacing each letter with a different letter a fixed number of positions down the alphabet.
As civilizations evolved, so did the methods of cryptography. The ancient Greeks used a technique called the Caesar Cipher, which involved shifting each letter by a fixed number of positions. The Romans also used a similar technique, known as the Vigenère cipher.
In modern times, the use of codes and ciphers has become increasingly sophisticated. The development of computers and algorithms has enabled the creation of complex encryption methods, making it more difficult for unauthorized parties to intercept and decode sensitive information.
Types of Military Code
There are several types of military code used for communication, each with its unique characteristics and methods. Some of the most common types of military code include:
- Substitution ciphers: This type of cipher involves replacing each letter with a different letter or symbol.
- Transposition ciphers: This type of cipher involves rearranging the letters of the message according to a specific pattern.
- Block ciphers: This type of cipher involves dividing the message into fixed-length blocks and encrypting each block separately.
- Stream ciphers: This type of cipher involves encrypting the message one bit or byte at a time.
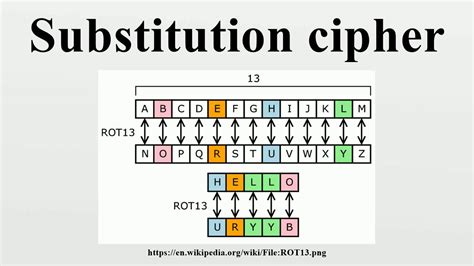
Numbers in Military Code
Numbers play a crucial role in military code, particularly in substitution ciphers and transposition ciphers. In substitution ciphers, numbers are used to replace each letter with a different letter or symbol. For example, the Caesar Cipher uses a simple substitution technique, where each letter is shifted by a fixed number of positions.
In transposition ciphers, numbers are used to rearrange the letters of the message according to a specific pattern. For example, the Vigenère cipher uses a series of numbers to determine the pattern of substitution.
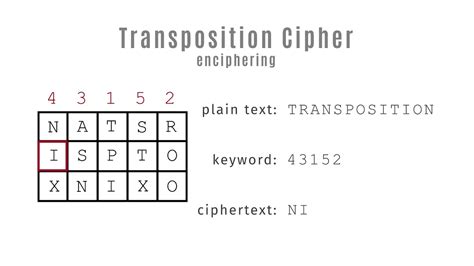
Techniques for Decoding Military Code
Decoding military code requires a combination of technical skills and analytical thinking. Some of the techniques used for decoding military code include:
- Frequency analysis: This technique involves analyzing the frequency of letters and symbols in the message to identify patterns and anomalies.
- Cryptanalysis by permutations: This technique involves analyzing the permutations of letters and symbols in the message to identify patterns and anomalies.
- Brute force attack: This technique involves trying all possible combinations of keys and codes to decrypt the message.

Modern Military Code
Modern military code uses advanced algorithms and techniques to ensure secure communication. Some of the modern techniques used in military code include:
- Public-key cryptography: This technique involves using a pair of keys, one public and one private, to encrypt and decrypt messages.
- Symmetric-key cryptography: This technique involves using the same key for both encryption and decryption.
- Hash functions: This technique involves using a one-way function to encrypt and decrypt messages.
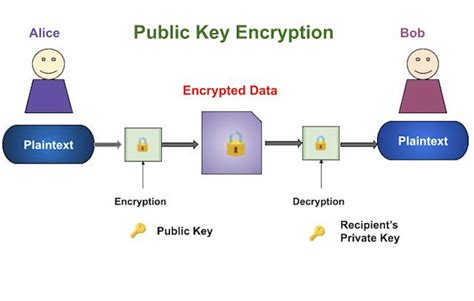
Challenges in Decoding Modern Military Code
Decoding modern military code is a complex task that requires advanced technical skills and analytical thinking. Some of the challenges in decoding modern military code include:
- Complexity of algorithms: Modern military code uses complex algorithms that are difficult to break.
- Limited computational resources: Decoding modern military code requires significant computational resources, which can be a challenge.
- Limited information: Decoding modern military code often requires limited information, which can make it difficult to identify patterns and anomalies.

Conclusion
Numbers play a crucial role in military code, particularly in substitution ciphers and transposition ciphers. Understanding numbers in military code requires knowledge of various techniques and methods, including frequency analysis, cryptanalysis by permutations, and brute force attack. Modern military code uses advanced algorithms and techniques to ensure secure communication, making it a complex task to decode.
If you have any questions or comments about numbers in military code, please feel free to share them in the comments section below.
Military Code Image Gallery





What is military code?
+Military code is a system of encrypting and decrypting messages to ensure secure communication.
What is the difference between substitution ciphers and transposition ciphers?
+Substitution ciphers involve replacing each letter with a different letter or symbol, while transposition ciphers involve rearranging the letters of the message according to a specific pattern.
What are some common techniques used for decoding military code?
+Some common techniques used for decoding military code include frequency analysis, cryptanalysis by permutations, and brute force attack.
