Intro
Unlock the complexities of cyber operations and stay ahead of the threats. Discover 5 critical ways to understand cyber operations, including threat intelligence, network exploitation, and cybersecurity strategies. Learn how to navigate the cyber landscape, anticipate attacks, and develop effective countermeasures to safeguard your digital assets.
Cyber operations have become a crucial aspect of modern warfare, national security, and even business operations. As technology advances, the need to understand cyber operations has become increasingly important. Cyber operations involve the use of computer systems and networks to disrupt, disable, or destroy an adversary's capabilities. In this article, we will explore five ways to understand cyber operations and their significance in today's digital age.
What are Cyber Operations?
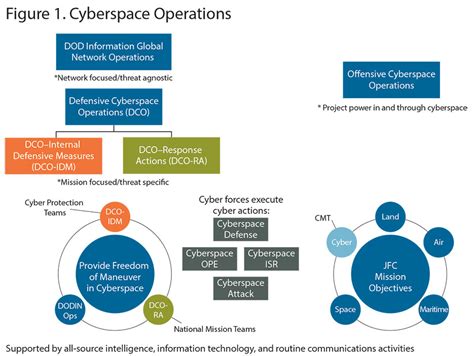
Cyber operations are a type of military operation that uses computer systems and networks to achieve strategic objectives. These operations can be used to disrupt an adversary's command and control systems, steal sensitive information, or destroy critical infrastructure. Cyber operations can be conducted by nation-states, terrorist organizations, or even individual hackers.
Types of Cyber Operations
There are several types of cyber operations, including:
- Network exploitation: This involves using computer networks to gather sensitive information about an adversary.
- Network attack: This involves using computer networks to disrupt or destroy an adversary's capabilities.
- Network defense: This involves using computer networks to defend against an adversary's cyber attacks.
- Cyber espionage: This involves using computer systems and networks to steal sensitive information about an adversary.
Understanding Cyber Operations through History

One way to understand cyber operations is to study their history. Cyber operations have been used in various forms since the 1980s, but they gained significant attention during the 1990s and 2000s. One notable example is the "I Love You" virus, which was released in 2000 and infected millions of computers worldwide. This virus was a significant wake-up call for the importance of cybersecurity and the need to understand cyber operations.
Another notable example is the Stuxnet worm, which was discovered in 2010. Stuxnet was a highly sophisticated cyber attack that targeted Iran's nuclear program. The worm was designed to sabotage the centrifuges used in Iran's nuclear program, and it is widely believed to have been created by the United States and Israel.
Key Players in Cyber Operations
There are several key players involved in cyber operations, including:
- Nation-states: Many nation-states have developed sophisticated cyber capabilities, including the United States, China, Russia, and North Korea.
- Terrorist organizations: Some terrorist organizations, such as ISIS, have developed cyber capabilities to disrupt and destroy their adversaries.
- Individual hackers: Individual hackers, such as those involved in the "I Love You" virus, can also conduct cyber operations.
Understanding Cyber Operations through Technology

Another way to understand cyber operations is to study the technology involved. Cyber operations rely heavily on computer systems and networks, as well as various types of software and hardware. Some key technologies used in cyber operations include:
- Malware: Malware is a type of software that is designed to harm or exploit computer systems.
- Trojans: Trojans are a type of malware that allow an attacker to gain unauthorized access to a computer system.
- Spyware: Spyware is a type of malware that is designed to steal sensitive information about a computer system or its user.
Cyber Operations and Artificial Intelligence
Artificial intelligence (AI) is playing an increasingly important role in cyber operations. AI can be used to improve the effectiveness of cyber attacks, as well as to defend against them. Some key applications of AI in cyber operations include:
- Predictive analytics: AI can be used to predict when and where cyber attacks are likely to occur.
- Automated incident response: AI can be used to automate the incident response process, reducing the time and effort required to respond to cyber attacks.
- Cyber threat hunting: AI can be used to hunt for cyber threats, identifying potential vulnerabilities and alerting defenders to take action.
Understanding Cyber Operations through Strategy
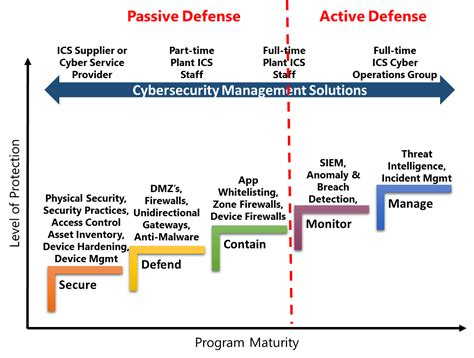
Cyber operations are also closely tied to strategy. Cyber operations can be used to support a wide range of strategic objectives, including:
- Deterrence: Cyber operations can be used to deter an adversary from taking certain actions.
- Disruption: Cyber operations can be used to disrupt an adversary's capabilities, making it more difficult for them to achieve their objectives.
- Destruction: Cyber operations can be used to destroy an adversary's capabilities, making it impossible for them to achieve their objectives.
Key Principles of Cyber Operations Strategy
There are several key principles of cyber operations strategy, including:
- Integration: Cyber operations should be integrated with other forms of military power, such as air, land, and sea power.
- Agility: Cyber operations should be agile, allowing defenders to quickly respond to changing circumstances.
- Persistence: Cyber operations should be persistent, allowing defenders to maintain pressure on an adversary over time.
Understanding Cyber Operations through International Relations

Cyber operations are also closely tied to international relations. Cyber operations can be used to support a wide range of international objectives, including:
- Diplomacy: Cyber operations can be used to support diplomatic efforts, such as by disrupting an adversary's ability to communicate.
- Economic coercion: Cyber operations can be used to economically coerce an adversary, such as by disrupting their ability to conduct financial transactions.
- Military coercion: Cyber operations can be used to militarily coerce an adversary, such as by disrupting their ability to command and control their forces.
Key Challenges in Cyber Operations and International Relations
There are several key challenges in cyber operations and international relations, including:
- Attribution: It can be difficult to attribute cyber operations to a specific actor, making it challenging to respond effectively.
- Escalation: Cyber operations can escalate quickly, making it challenging to control the consequences.
- Norms: There is a need for norms and standards in cyber operations, to help guide the behavior of actors and prevent unintended consequences.
Understanding Cyber Operations through Culture

Finally, cyber operations are also closely tied to culture. Cyber operations can reflect the culture and values of a society, and can also be influenced by cultural factors. Some key cultural factors that influence cyber operations include:
- Values: Cyber operations can reflect the values of a society, such as the importance of individual freedom or the need for national security.
- Norms: Cyber operations can be influenced by cultural norms, such as the norm of not conducting cyber attacks against civilians.
- Language: Cyber operations can be influenced by language, with some languages being more conducive to cyber operations than others.
Key Cultural Factors in Cyber Operations
There are several key cultural factors in cyber operations, including:
- Cybersecurity culture: A culture of cybersecurity can help to prevent cyber attacks and protect against them.
- Digital literacy: A culture of digital literacy can help to ensure that people have the skills and knowledge needed to operate safely in the digital world.
- Cyber awareness: A culture of cyber awareness can help to ensure that people are aware of the risks and consequences of cyber operations.
Cyber Operations Image Gallery
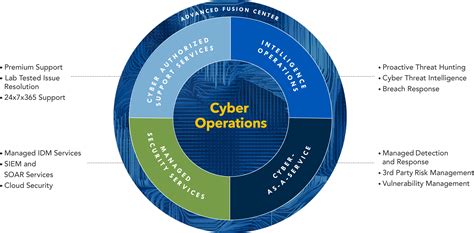






What are cyber operations?
+Cyber operations are a type of military operation that uses computer systems and networks to achieve strategic objectives.
What are the different types of cyber operations?
+There are several types of cyber operations, including network exploitation, network attack, network defense, and cyber espionage.
What is the significance of cyber operations in today's digital age?
+Cyber operations are significant because they can be used to disrupt or destroy an adversary's capabilities, and can also be used to support a wide range of strategic objectives.
In conclusion, cyber operations are a complex and multifaceted topic that requires a deep understanding of technology, strategy, international relations, and culture. By studying the history of cyber operations, the technology involved, and the strategic and cultural factors that influence them, we can gain a better understanding of this important topic. We hope this article has provided valuable insights into the world of cyber operations, and we encourage readers to continue exploring this fascinating topic.
