Intro
Discover the critical role of cyber security in modern military operations. Learn how advanced threats, IoT vulnerabilities, and AI-powered attacks impact national security. Explore the latest strategies for protecting military networks, securing sensitive data, and maintaining operational superiority in the digital battlefield.
The increasing dependence on technology in modern military operations has made cyber security a critical aspect of national defense. As military forces rely more heavily on digital systems to communicate, coordinate, and execute operations, the risk of cyber attacks and data breaches has grown exponentially. In this article, we will explore the importance of cyber security in modern military operations and examine the various measures being taken to protect military networks and systems from cyber threats.

The Threat of Cyber Attacks in Military Operations
Cyber attacks pose a significant threat to modern military operations, as they can compromise the security and integrity of sensitive information and disrupt critical systems. A successful cyber attack can have devastating consequences, including the loss of sensitive information, disruption of command and control systems, and even the loss of life.
One of the most significant risks associated with cyber attacks is the potential for an adversary to gain access to sensitive information, such as military plans, troop movements, and communication networks. This information can be used to gain a strategic advantage over military forces, making it more difficult to execute operations effectively.
Another risk associated with cyber attacks is the potential for disruption of critical systems, such as communication networks, navigation systems, and logistics systems. These systems are essential to the effective execution of military operations, and a disruption can have significant consequences.
There are several types of cyber threats that military forces must be aware of, including:
- Malware: Malware is software that is designed to harm or exploit a computer system. It can be used to steal sensitive information, disrupt critical systems, or take control of a system.
- Phishing: Phishing is a type of cyber attack that involves tricking individuals into revealing sensitive information, such as passwords or credit card numbers.
- Denial of Service (DoS): A DoS attack involves overwhelming a system with traffic in order to make it unavailable to users.
- Advanced Persistent Threats (APTs): APTs are sophisticated cyber attacks that involve the use of multiple vectors to gain access to a system and remain undetected for an extended period.
Cyber Security Measures in Modern Military Operations
To protect against cyber threats, military forces are implementing a range of cyber security measures, including:
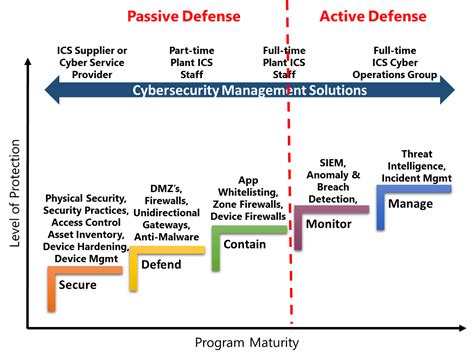
- Network Security: Network security involves the use of firewalls, intrusion detection systems, and encryption to protect military networks from cyber threats.
- Threat Intelligence: Threat intelligence involves the collection and analysis of information about potential cyber threats in order to anticipate and prepare for attacks.
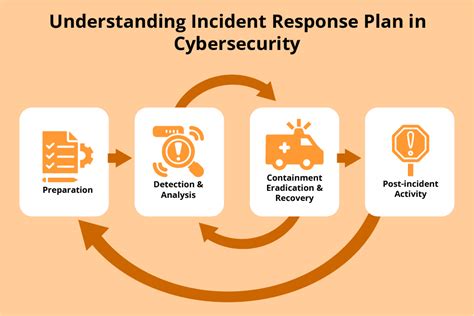
- Incident Response: Incident response involves the development of plans and procedures for responding to cyber attacks, including the identification of the source of the attack, containment of the attack, and eradication of the threat.
- Cyber Security Training: Cyber security training involves the education of military personnel on cyber security best practices, including the use of strong passwords, the avoidance of suspicious emails and attachments, and the use of encryption.

Cyber Security Challenges in Military Operations
Despite the importance of cyber security in modern military operations, there are several challenges that military forces must overcome, including:
- Limited Resources: Cyber security requires significant resources, including personnel, equipment, and funding. Military forces often have limited resources, making it difficult to implement effective cyber security measures.
- Complexity: Cyber security is a complex and rapidly evolving field, making it difficult for military forces to keep up with the latest threats and technologies.
- Interoperability: Military forces often use a range of different systems and networks, making it difficult to ensure interoperability and consistency in cyber security measures.
Future of Cyber Security in Modern Military Operations
The future of cyber security in modern military operations is likely to involve the use of advanced technologies, such as artificial intelligence and machine learning, to detect and respond to cyber threats. Military forces are also likely to place greater emphasis on cyber security training and awareness, as well as the development of more effective incident response plans.

Conclusion
Cyber security is a critical aspect of modern military operations, and military forces must take steps to protect against cyber threats. This includes the implementation of network security measures, threat intelligence, incident response plans, and cyber security training. Despite the challenges associated with cyber security, military forces must prioritize this aspect of their operations in order to ensure the security and integrity of sensitive information and critical systems.
Cyber Security in Modern Military Operations Image Gallery








What is the importance of cyber security in modern military operations?
+Cyber security is critical in modern military operations as it protects sensitive information and critical systems from cyber threats, ensuring the security and integrity of military operations.
What are the types of cyber threats that military forces must be aware of?
+Military forces must be aware of malware, phishing, denial of service (DoS) attacks, and advanced persistent threats (APTs).
What measures can military forces take to protect against cyber threats?
+Military forces can implement network security measures, threat intelligence, incident response plans, and cyber security training to protect against cyber threats.
