The concept of restricted access has become increasingly important in today's world, where security and privacy are major concerns. Restricted access refers to the limitation or control of access to certain resources, information, or areas. This can be achieved through various means, including physical barriers, technological measures, or administrative controls. In this article, we will explore five ways restricted access can be implemented and their significance in different contexts.
Physical Barriers for Restricted Access
Physical barriers are one of the most common methods of restricting access. This can include fences, gates, doors, and locks. For instance, a company may install a fence around its premises to prevent unauthorized entry. Similarly, a door with a lock can restrict access to a particular room or area. Physical barriers are effective in controlling access to sensitive areas or resources.
Technological Measures for Restricted Access
Technological measures are another way to restrict access. This can include biometric authentication, such as fingerprint or facial recognition, and digital access control systems. For example, a company may use a biometric authentication system to control access to its server room. Similarly, a digital access control system can be used to restrict access to certain areas or resources based on an individual's role or permissions.
Administrative Controls for Restricted Access
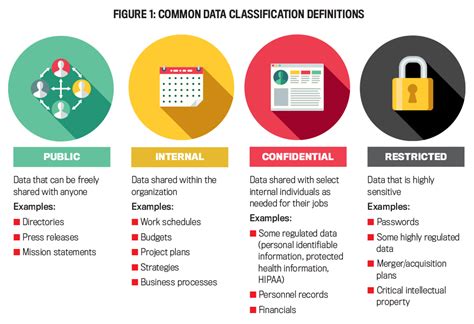
Administrative controls refer to the policies and procedures put in place to restrict access. This can include background checks, clearance procedures, and access protocols. For instance, a government agency may conduct background checks on individuals before granting them access to classified information. Similarly, a company may have clearance procedures in place to ensure that only authorized personnel have access to sensitive areas or resources.
Network Security Measures for Restricted Access
Network security measures are crucial in restricting access to digital resources. This can include firewalls, intrusion detection systems, and encryption. For example, a company may use a firewall to block unauthorized access to its network. Similarly, an intrusion detection system can be used to detect and prevent cyber attacks.
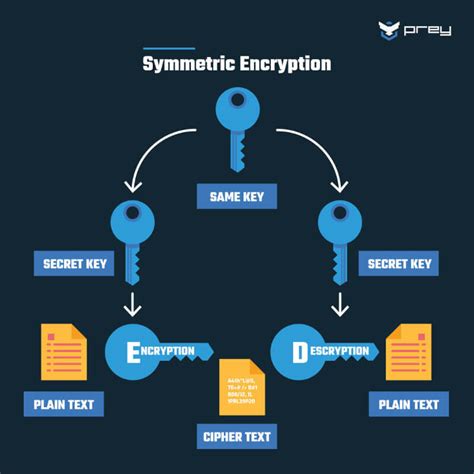
Data Encryption for Restricted Access
Data encryption is a method of restricting access to sensitive information. This involves converting plaintext data into unreadable ciphertext, which can only be deciphered with the decryption key. For instance, a company may use encryption to protect its customer data from unauthorized access. Similarly, encryption can be used to restrict access to sensitive information, such as financial data or personal identifiable information.
Benefits of Restricted Access
The benefits of restricted access are numerous. It helps to prevent unauthorized access, protect sensitive information, and reduce the risk of cyber attacks. Restricted access also helps to ensure compliance with regulatory requirements, such as data protection laws. Additionally, it can help to prevent data breaches, which can have serious consequences, including financial losses and reputational damage.
Challenges of Implementing Restricted Access
Implementing restricted access can be challenging. It requires significant investment in technology, infrastructure, and personnel. Additionally, it can be difficult to balance the need for security with the need for accessibility. Overly restrictive access controls can hinder productivity and efficiency, while inadequate controls can leave an organization vulnerable to security threats.
Best Practices for Implementing Restricted Access
To implement restricted access effectively, organizations should follow best practices. This includes conducting risk assessments to identify vulnerabilities, implementing multi-factor authentication, and regularly reviewing and updating access controls. Additionally, organizations should provide training to employees on access protocols and procedures, and ensure that access controls are aligned with business objectives.
Restricted Access Image Gallery
What is restricted access and why is it important?
+
Restricted access refers to the limitation or control of access to certain resources, information, or areas. It is important because it helps to prevent unauthorized access, protect sensitive information, and reduce the risk of cyber attacks.
What are the different types of restricted access?
+
There are several types of restricted access, including physical barriers, technological measures, administrative controls, network security measures, and data encryption.
How can organizations implement restricted access effectively?
+
Organizations can implement restricted access effectively by conducting risk assessments, implementing multi-factor authentication, regularly reviewing and updating access controls, providing training to employees, and ensuring that access controls are aligned with business objectives.
In conclusion, restricted access is a critical component of security and privacy in today's world. By implementing restricted access measures, organizations can protect sensitive information, prevent unauthorized access, and reduce the risk of cyber attacks. It is essential for organizations to follow best practices and stay up-to-date with the latest technologies and trends to ensure effective implementation of restricted access. We invite you to share your thoughts and experiences on restricted access in the comments section below. Additionally, if you found this article informative, please share it with others who may benefit from it.